If you encrypt a secret message with a random key that is as long as the message itself, your cipher will not be crackable. This is called the One-Time-Pad encryption. But, of course, your communication partner must have the same key, and you cannot use the same key twice. So how do you distribute a secret key between two parties without meeting in person? Quantum cryptography, or better, quantum key distribution has the solution: Use quantum information!
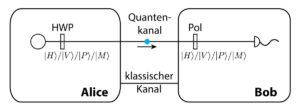
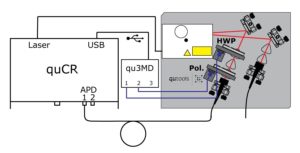
The most famous protocol implementing secure key distribution is the BB84 protocol. Here, Alice sends single photons randomly polarized horizontally or vertically (straight base), or +45° or -45° (diagonal base). In our setup, we use weak coherent pulses with adjustable average photon numbers and a half-waveplate to switch between . Bob, on the other hand, uses a polarizer also set randomly to these angles and tries to detect the single photons.
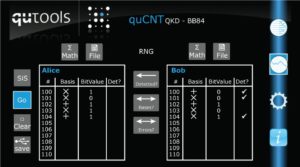
After detecting the photons, they can communicate openly on a clasical channel (normally the internet, but since we only have an educational setup this is done internally in the quCR control unit) which photons were detected and compare their bases. After an error correction protocol, they will have the same key, ready to use for One-Time-Pad encryption!
Why is this key distribution scheme secure? Can you imagine which attacks an eavesdropper (Eve) could perform? Can you defend against them? Find out by experimenting on your own with the quED-QKD AddOn.
What do you need?
Connected Experiments
- Quantum Random Number Generation
- Particle Nature of Photons
- Interaction-Free Measurement (Bomb Test)

 Interferometers
Interferometers Time-Tagger
Time-Tagger Quantum Physics Kits
Quantum Physics Kits